IT & Tech Teams
One system to unify them all
Between managing a complex set of student and faculty systems and doing hefty system replacement projects, offering students a modern, centralized user interface may seem like a bridge too far. Not anymore. Pathify revolutionizes the student experience by centralizing all your important systems into a secure, cloud-based platform that’s easy for users to navigate, accessible from any device (web or mobile) and acts as a reliable student facing bridge during major system replacements (like your SIS or LMS).
Engagement Hub
A window into every system
What if you offered students a single point of access to all of your systems? Imagine how much engagement would increase.
Pathify plays the role of hub to all institutional systems, creating a centralized user interface that pulls in important information, tools, resources and data from every source system. Students spend less time grappling with logins and easily navigate their experience on whatever device is handy — web or mobile. Talk about a win-win.
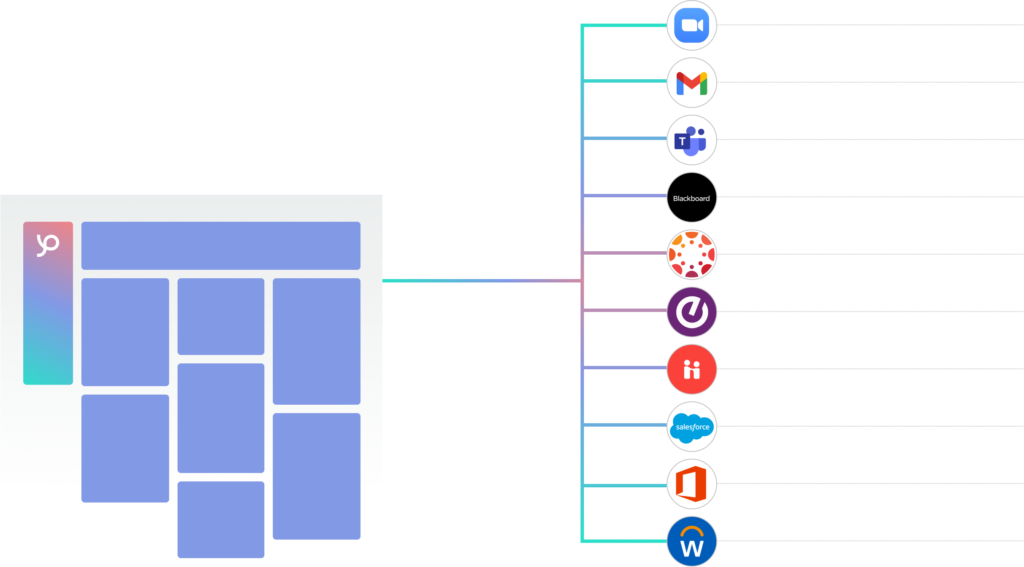
SIS
Pull in vital student information like GPA, major and course completion tracking from your student information system.
LMS
Display course information, deadlines and grades in the same platform as everything else instead of making students log into a separate LMS.
Productivity Suite
Surface a student’s most recent emails and files from Office 365 or Google Workspace to make everything easy to find.
SSO
One secure login makes it easy for students to access whatever they need. Pathify integrates with your existing authentication mechanism for SSO.
Personalization
A role for every user
Many systems use role-based permissions to personalize what users see and do. Why should the student experience be any different?
Pathify lets you create roles to immediately surface the exact information each user needs for a personalized, easy-to-use experience. Roles can be as broad or as granular as your institution chooses to easily target subgroups of users.
Device Agnostic
True mobile-web parity fits today’s users
Today’s students use their mobile devices for everything, but many institutions still don’t offer a cohesive, functional native mobile app (a disconnected mobile app and web portal don’t count). Offering students a consistent experience accessible via web or mobile meets their expectations for how technology should work.
Secure
More features, less worry
Pathify is cloud-based, continuously maintained and updated, and follows industry-leading security protocols. IT leaders review and approve our security patching, authentication, protocol and sessions security, data access, backup and recovery, and physical data security.